The 7-Second Trick For Cyber Security Awareness
CISO tasks range commonly to preserve enterprise cybersecurity. IT professionals as well as other computer specialists are required in safety roles, such as: is the person that carries out the safety program across the organization and oversees the IT safety and security department's procedures. is the executive responsible for the physical and/or cybersecurity of a company.
concentrates on keeping software program and devices devoid of dangers. A jeopardized application could supply access to the data its designed to secure. Successful protection begins in the layout phase, well before a program or gadget is deployed. protects the honesty as well as personal privacy of information, both in storage as well as in transit.
The consents users have when accessing a network and also the procedures that identify just how and also where data may be saved or shared all loss under this umbrella. define just how a company responds to a cyber-security incident or any kind of other occasion that triggers the loss of procedures or data. Calamity recuperation plans determine how the company restores its procedures as well as information to return to the very same operating capability as before the event.
The Ultimate Guide To Cyber Security Awareness
Cybercriminals fool individuals into submitting Trojans onto their computer where they trigger damage or gather data. A program that secretly tapes what a user does, to ensure that cybercriminals can take advantage of this details. For instance, spyware can capture charge card details. Malware which secures down a customer's data as well as information, with the threat of eliminating it unless a ransom is paid.

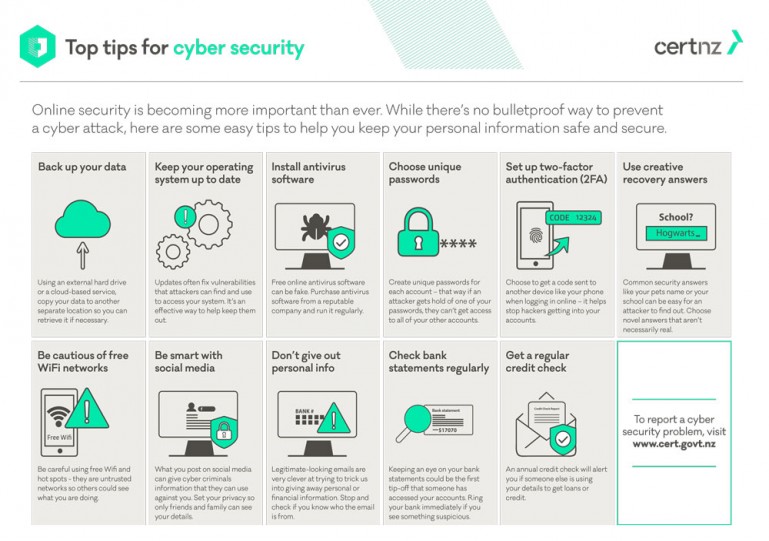
This implies you profit from the most up to date safety and security patches. 2. Protection solutions like Kaspersky Overall Security will certainly discover as well as gets rid of dangers. Maintain your software program upgraded for the ideal level of security. 3. Guarantee your passwords are not easily guessable. 4. These could be infected with malware. 5. This is a typical method that malware is spread out.
As applications play an increasingly critical role in organization, it is vital to concentrate on web application safety. Network safety is the process of her latest blog safeguarding the functionality and integrity of your network and information. This is achieved by performing a network penetration test, which examines your network for vulnerabilities and security issues.
The smart Trick of Cyber Security Awareness That Nobody is Discussing

This is because a number of these organizations: Can not pay for specialist IT solutions Have minimal time to dedicate to cyber protection Do not know where to begin Here are some of the most typical hazards among cyber strikes:: Malware, also known as malicious software application, is invasive software program established by cyber criminals to take information or to harm as well as destroy computers and computer systems, useful source according to CISCO.
Here are one of the most common kinds of cyber safety readily available:: Application safety defines security used by applications to avoid data or code within the application from being stolen or pirated. These safety systems are applied throughout application growth however are created to secure the application after release, according to VMWare.
The Io, T is a network of connected things as well as people, all of which share data regarding the method they are made use of as well as their settings, according to IBM. These gadgets consist of home appliances, sensors, televisions, routers, printers as well as countless other residence network tools. Safeguarding these gadgets is very important, as well as according to a study by Bloomberg, safety is among the biggest barriers to extensive Io, T adaption.
The smart Trick of Cyber Security Awareness That Nobody is Talking About
Petitto always intended to work within the IT field, as well as he picked cyber safety and security because it's a greatly expanding area. He moved credit histories from a neighborhood university with a united state Flying force program and completed his bachelor's in under 2 years. "It was much quicker than I thought it would certainly be," he stated.
"Even prior to completing (my) degree, I obtained several invites to speak with for entry-level placements within the sector and received three work deals," claimed Petitto. He chose to stay within the Air Pressure as well as transfer to a cyber security unit as opposed to signing up with the personal field.
Bureau of Labor Stats (BLS) forecasts that employment for info protection analysts will certainly grow by 33% via 2030. That's even more than twice as fast as the average computer-related occupation and also 4 click this times as quick as American tasks generally. To assist load the demand for more professionals in the cyber safety and security globe, Cyber, Seek, a job funded by the federal government and supported by market companions, supplies in-depth information on the need for these employees by state.
Meanwhile, bigger firms may have entire departments committed to safeguarding information and also ferreting out hazards. While business define functions relevant to details safety and security in a selection of ways, Kamyck claimed there are some details tasks that these staff members are typically gotten in touch with to do. Oftentimes, they need to evaluate dangers as well as collect details from a firm's web servers, cloud solutions as well as employee computers as well as mobile gadgets (Cyber Security Awareness).